
Introduction
Application authentication methods, such as certificates and password secrets, are essential for apps to acquire tokens and access data in Microsoft Entra ID. IT administrators can enforce best practices for using these authentication methods through specific policies. This article explores how these policies work, their importance, and how to manage them effectively using Microsoft Entra ID portal.What Are Application Authentication Methods Policies?
Application authentication methods policies allow IT admins to control how applications use various authentication methods. These policies can:- Block the use of certain authentication methods.
- Limit the lifetime of password secrets.
- Enforce restrictions based on the creation date of the application or service principal.
Key Benefits
- Enhanced Security: By enforcing these policies, organizations can take advantage of new app security hardening features, review their current security posture, and implement necessary controls.
- Flexibility: Policies can be tailored for individual applications or service principals, providing granular control.
- Scalability: Policies can be enforced for new applications as well as existing ones, ensuring consistent security standards.
Types of Policy Controls
- Tenant Default Policy: Applies to all applications or service principals within a tenant. This policy is created by default but is disabled until configured.
- App Management Policies: Allows for the inclusion or exclusion of individual applications from the tenant default policy, providing more specific control.
Tenant Default App Management Policy
The tenant default policy is a single object that always exists but is disabled by default. It includes:- Application Restrictions: Target applications owned by the tenant.
- Service Principal Restrictions: Target applications provisioned from another tenant.
These restrictions help lock down credential usage in apps originating from the tenant and control credential addition in externally provisioned applications.
Multi-Tenant Apps (Homed in Customer Tenant): Apply the policy to the application object.
Multi-Tenant Apps (Provisioned from Another Tenant): Apply the policy to the service principal object.

Licensing: All app policy management operations require a Microsoft Entra Workload ID Premium license.
1. Open your browser and navigate to https://entra.microsoft.com
2. Go to the "Protection" tab.
3. Click on "Authentication Methods."
4. Select "Application Policies."
Let's establish password restrictions for the application registration based on the default policy.
For our testing case, follow these steps:
1. Select values for "Password Addition."
2. Set the "Password Lifetime."
3. Optionally, if desired, apply the same settings to Enterprise Apps by selecting "Copy setting selection to enterprise apps."
Example Selection as Follows: For password addition, applications created after June 2, 2024.App Management Policy for Applications and Service Principals
App management policies can be defined in the appManagementPolicy resource, containing various restrictions or different enforcement dates from the tenant default policy. When both policies exist, the app management policy takes precedence, and the assigned application or service principal doesn't inherit from the tenant default policy.Restrictions Managed in Microsoft Entra ID
The application authentication methods policy offers several restrictions, including:- Password Addition: Restricts adding new password secrets to applications.
- Password Lifetime: Enforces a maximum lifetime for password secrets.
- Custom Password Addition: Restricts adding custom password secrets.
- Symmetric Key Addition: Blocks adding new symmetric keys.
- Symmetric Key Lifetime: Enforces a maximum lifetime for symmetric keys.
- Asymmetric Key Lifetime: Enforces a maximum lifetime for asymmetric key credentials (certificates).
Applying Policies Based on App Type
Single-Tenant Apps: Apply the policy to the application object.Multi-Tenant Apps (Homed in Customer Tenant): Apply the policy to the application object.
Multi-Tenant Apps (Provisioned from Another Tenant): Apply the policy to the service principal object.
Summary of Key Differences

Application Authentication Method Policy Requirements
Roles: The least privileged roles for managing these policies are Application Administrator and Cloud Application Administrator.Licensing: All app policy management operations require a Microsoft Entra Workload ID Premium license.
How to configure Application Authentication Policies
To create an application authentication method policy, follow these steps:1. Open your browser and navigate to https://entra.microsoft.com
2. Go to the "Protection" tab.
3. Click on "Authentication Methods."
4. Select "Application Policies."
Let's establish password restrictions for the application registration based on the default policy.
For our testing case, follow these steps:
1. Select values for "Password Addition."
2. Set the "Password Lifetime."
3. Optionally, if desired, apply the same settings to Enterprise Apps by selecting "Copy setting selection to enterprise apps."
For password lifetime, applications created after May 30, 2024, with a maximum lifetime of 90 days.
Optionally selected Copy setting selection to Enterprise Apps
Here is a list of applications on the tenant along with their creation dates.
Let's select the WPMail application, which was created on June 3, 2024, and examine the password creation restrictions applied to it.
Let's select the WPMail application, which was created on June 3, 2024, and examine the password creation restrictions applied to it.
It's evident that the policy has been successfully applied to the application.
It's evident that the policy is in effect, and the maximum lifetime for secret creation is limited to 90 days.
Note: Custom application policies affect selected app registrations and enterprise apps. The restrictions in these polices will override the ones enabled in the 'Default policy
To create custom application policies, navigate to the "Same Application Policies" section and select "Custom Application Policies."
Click on "New Custom Policy" and in the upcoming window, provide a policy name and description and click Next
In the upcoming password restrictions section, we will select the settings as indicated in the screenshot below. Additionally, we will include symmetric key addition restrictions for testing purposes. Click Next to proceed with the remaining settings
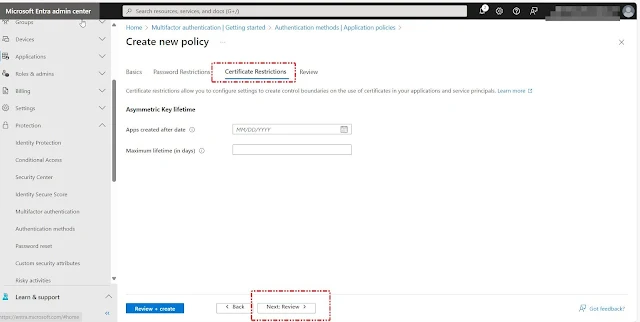
Certificate Restrictions we will not configure now. Click Next and Review the settings
Note: Certificate restrictions allow you to configure settings to create control boundaries on the use of certificates in your applications and service principals
Now that our custom application policy has been created, let's proceed to add the application and enable this policy.
Click on our policy to open it, then scroll all the way down and click on the "Add Apps" section.
We are adding two applications for testing the custom policy.
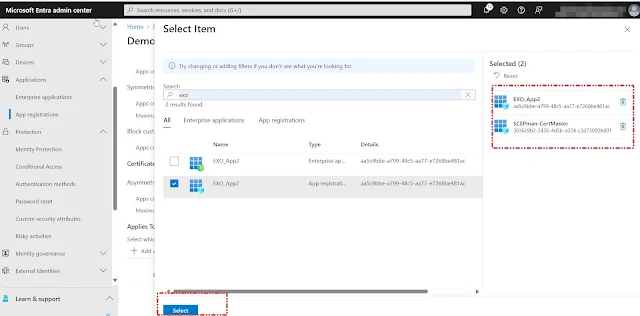
Click the "Enable Policy" button to activate the policy.
Now lets test the Application Secret creation
Lets Validate the Secret Expiry Policy using our second application






























0 Comments