Introduction
Managing applications in Microsoft Entra ID (formerly Azure AD) is crucial for enterprise developers and SaaS providers. Applications registered on the Microsoft identity platform rely on two key components: Application Objects and Service Principal Objects. This blog will explore these concepts, their relationship, and the steps to restore or remove recently deleted applications, including enterprise applications and app registrations.Understanding Application Objects and Service Principal Objects
Application Registration in Microsoft Entra ID
Key Outcomes of Application Registration
- Globally Unique Instance: Upon successful registration, a globally unique application object is created within the home tenant (the tenant where the app is registered). This object includes a unique App ID (also known as the client ID) used to identify the application.
- Configuration Options: After registration, you can:
- Add secrets or certificates to secure communication.
- Define API permissions and scopes.
- Customize branding, such as the sign-in dialog and logos.
- For applications registered directly through the Microsoft Entra admin center, both an application object and a service principal are created automatically in the home tenant.
- When using Microsoft Graph APIs for registration, creating the service principal is a separate step.
The Application Object: Blueprint of the Application
The application object represents a single, global definition of the application and resides exclusively in the home tenant. It serves as the blueprint for creating service principal objects, which are tenant-specific implementations.
Characteristics of an Application Object
- Static Configuration: Certain properties, like App ID and permissions, are inherited by all service principal objects derived from the application object.
- Global Scope: The application object applies universally, regardless of the number of tenants where the app is used.
Key Roles of the Application Object
- Token Issuance: Defines how the app issues tokens for authentication.
- Resource Access: Lists the resources the app can access.
- App Actions: Specifies what the app can do, such as read or modify data.
You can manage application objects via the App Registrations page in the Microsoft Entra admin center or programmatically through Microsoft Graph APIs.
The Service Principal Object: Tenant-Specific Representation
A service principal is the local, tenant-specific representation of the global application object. It acts as the identity of the application in a specific tenant, allowing it to access resources within that tenant.
Types of Service Principals
- Application Service Principal:
- Created for each tenant where the app is used.
- Represents a specific instance of the application.
- Inherits key properties from the application object.
2. Managed Identity Service Principal:
- Automatically created when an Azure resource is assigned a managed identity.
- Provides secure access to resources without needing credentials.
- Cannot be modified directly.
3. Legacy Service Principal:
- Represents apps created before the introduction of app registrations or legacy systems.
- Typically lacks an associated application object.
Responsibilities of Service Principals
- Authentication: Authenticates the app when it attempts to sign in to the tenant.
- Authorization: Enforces access policies and permissions for the app.
- Custom Configuration: Allows tenant-specific settings like user assignments and Conditional Access policies.
Relationship Between Application Objects and Service Principals
The relationship between an application object and service principals is central to the multi-tenant architecture of Microsoft Entra ID:
- One-to-One with Software Application: Each application object corresponds to a single software application.
- One-to-Many with Service Principals: A single application object can have multiple service principals, one for each tenant where the app is used.
Example: Single vs. Multi-Tenant Applications
- Single-Tenant Application:
- Has only one service principal in its home tenant.
- Intended for use within the home tenant only.
- Multi-Tenant Application:
- The home tenant hosts the application object and a service principal.
- Additional service principals are created in each tenant where the app is used, upon admin or user consent.
Viewing and Managing Application and Service Principal Objects
Application Objects
You can view and manage application objects in the App Registrations section of the Microsoft Entra admin center. Actions include:
- Editing app configurations.
- Managing secrets and certificates.
- Reviewing API permissions.
Service Principals
Service principals can be managed from the Enterprise Applications page. Available actions include:
- Viewing permissions and consent history.
- Assigning users or groups to the application.
- Configuring Conditional Access policies.
Practical Use Case: Token Issuance and Access Permissions
Consider an HR management system used by multiple companies:
1. Home Tenant (Adatum):
- The application is registered, creating the application object.
- A service principal is also created for the application in Adatum.
2. Consumer Tenants (Contoso, Fabrikam):
- Service principals are created in these tenants when admins grant consent for the app.
- Each service principal has tenant-specific permissions based on the granted scopes.
If the application is deleted in Adatum, the service principal in Adatum is also deleted, but the service principals in Contoso and Fabrikam remain intact.
Application Interaction with Microsoft Entra ID
To enable seamless identity and access management, applications must be registered with Microsoft Entra ID. This registration process involves creating an application object and a corresponding service principal in the application's home tenant. Managing applications in Microsoft Entra ID includes creating, configuring, monitoring, and maintaining these applications within a secure cloud environment.
When an application is registered in a Microsoft Entra tenant, users assigned to the application can securely access it. Microsoft Entra ID supports the registration and management of various types of applications, enabling flexibility for different business scenarios. These include preintegrated applications, custom-developed applications, and on-premises applications.
Application Types in Microsoft Entra ID
1.Preintegrated Applications
Microsoft Entra ID provides a gallery of preintegrated applications (referred to as "Cloud Applications"), which can be configured with minimal effort. These applications are preconfigured for seamless integration, and Microsoft provides detailed guides for setup. Using preintegrated applications reduces complexity and accelerates deployment.
Example:
To add a preintegrated application to your tenant, navigate to the Microsoft Entra admin center, select an application from the gallery, and follow the configuration steps outlined in its documentation.
Sign in to the Microsoft Entra admin center and navigate to Identity > Applications > Enterprise Applications. Use the search bar to locate the application you want to add. Note that only applications published in the Microsoft Entra application gallery can be added directly.
Let's add an application from the Enterprise Application Gallery, specifically Workday, to enable SAML-based Single Sign-On (SSO) between the application and Microsoft Entra ID.
Note: We will not configure SSO at this stage, as this is solely to demonstrate the application integration process.
The application has now been successfully added to our Microsoft Entra ID tenant, and we can view its properties and settings for further configuration.Now, if we navigate to the App Registrations section, we can see that the Workday application has been created and is linked to the corresponding Workday Enterprise Application Service Principal.
Create Your Own Application
If the application you’re looking for is not available, you can select Create your own application from the top menu to register a custom application.2. Custom-Developed Applications
If you develop your own business application, you can register it with Microsoft Entra ID to leverage its robust security features, such as Single Sign-On (SSO) and Conditional Access.
- Registration Options:
- App Registrations: Directly register your app and define its configuration.
- Enterprise Applications: Use the Create your own application link to register and manage your app.(Mentioned previously)
- Considerations for Integration: Evaluate how your application handles authentication and ensure it supports protocols like OpenID Connect or OAuth 2.0 for smooth integration with Microsoft Entra ID.
- Making Your App Available to Others: If you want to share your custom application with other organizations, you can submit it to the Microsoft Entra gallery, making it accessible to a broader audience.
Steps to Register an Application
Sign in to the Microsoft Entra admin center and navigate to Identity > Applications > App Registrations.3. On-Premises Applications
Organizations with on-premises applications can also benefit from Microsoft Entra ID's capabilities by connecting these applications through the Microsoft Entra Application Proxy or you can use Entra Private Access.
Managing Application Lifecycle: Deletion and Restoration
Soft Deletion of Applications
When an application is deleted, it moves to a soft-deleted state and is retained in the recycle bin for 30 days. This ensures accidental deletions can be recovered.
Note: Non-admin users are limited to 250 Microsoft Entra resources (active and deleted). Ensure you permanently delete unused objects to avoid exceeding this limit.
Let’s delete an application from the App Registrations section, which has a corresponding Service Principal in Enterprise Applications. During the deletion process, a warning message will appear, indicating that the application will no longer be able to sign in users or access protected resources, as it is used for Single Sign-On (SSO) with the Box application.
Box Application Service Principal deleted from Enterprise Applications
Consequences of Deletion
- Deleting an application object removes:
- The application object itself.
- The service principal in the home tenant.
- For multi-tenant applications:
- Service principals in other tenants remain unaffected.
- Conditional Access policies, provisioning data, and app proxy configurations associated with the service principal must be reconfigured upon recovery.
Restoring a Deleted Application
You can restore applications from the recycle bin during the 30-day soft-deletion window.
Steps to Restore an Application
- Sign in to the Microsoft Entra admin center.
- Navigate to Identity > Applications > App registrations > Deleted Applications.
- Search for the application and select Restore App Registration. In our case will restore Box Application for testing.
- Conditional Access policies (If required)
- App proxy configurations (If required)
Using PowerShell for Restoration
Run the following commands to restore a deleted application: You need to sign in as at least a Cloud Application Administrator.
Connect-MgGraph -Scopes "Application.ReadWrite.All"
Get-MgDirectoryDeletedItem -DirectoryObjectId <Object id>
Restore-MgDirectoryDeletedItem -DirectoryObjectId <Object id>
Permanent Deletion
Soft-deleted applications can be permanently deleted via the Entra admin center or PowerShell:
The screenshot below displays the available options.
Remove an application authored by another organization
When viewing App Registrations in the context of a tenant, some applications listed under the All Apps tab are from external tenants and were added to your tenant during the consent process. These applications are represented solely by a service principal object in your tenant, without a corresponding application object.
To remove an application's access to your directory after consent has been granted, the service principal must be deleted. This action requires administrative privileges, such as the Privileged Role Administrator role.
Deleting Enterprise Applications: Key Considerations
- Suspended State:
- When you delete an enterprise application, it enters a suspended state and moves to the recycle bin for 30 days.
- During this period, the application can be restored if needed.
- After 30 days, deleted applications are permanently removed.
- Prerequisites for Deletion:
- A Microsoft Entra user account
- One of the following roles:
- Cloud Application Administrator
- Application Administrator
- Owner of the service principal
- The enterprise application must already exist in your tenant.
Steps to Delete an Enterprise Application Using Entra ID Portal
In our testing, we will use the Quest On Demand - Migration - Mailbox Migration service principal, which was created as part of the Quest Mailbox Migration tool's integration with our Microsoft Entra ID tenant. This is a multi-tenant application registered on the Quest Entra ID tenant, meaning it does not have an app registration created in our tenant. This scenario aligns with the example we previously discussed for the HR application.
To proceed:
Navigate to Microsoft Entra Enterprise Applications.
Select the Quest application: Quest On Demand - Migration - Mailbox Migration.
Go to Properties and delete the application.
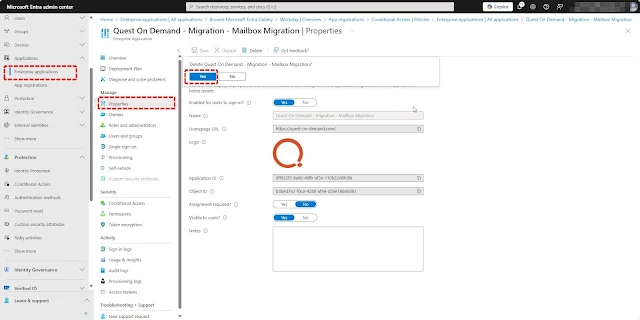
Application has been deleted
Steps to Delete an Enterprise Application Using Microsoft Graph PowerShell
Steps to Restore an Enterprise Application Using Microsoft Graph PowerShell
We will now restore the deleted application using the below Microsoft Graph Powershell
Restore-MgDirectoryDeletedItem -DirectoryObjectId <id>
We successfully restored two applications that were previously deleted:- One application deleted via the Microsoft Entra ID portal.
- Another application deleted using Microsoft Graph PowerShell.
The screenshot below shows the restored applications (service principals).
Warning: Permanently deleting an enterprise application is an irreversible action. Any present configurations on the app will be completely lost. Carefully review the details of the enterprise application to be sure you still want to hard delete it.
To permanently delete the soft deleted enterprise application, run the following command:
Note: You can't configure the periodicity of hard deletion
- A maximum of 100 users and service principals can be assigned as owners of a single application.
- Each user, group, or service principal can have up to 1,500 app role assignments. This limit applies collectively across all app roles, not to the number of assignments for a single app role.
- A user can configure credentials for up to 48 applications using password-based single sign-on (SSO). This limit applies only when the user is directly assigned to the application, not when assigned through a group.
- A group can also configure credentials for up to 48 applications using password-based SSO.
- The application manifest supports a maximum of 1,200 entries.
- Assigning groups to an application is supported; however, nested groups within the directly assigned group will not have access to the application.
Conclusion
Managing applications in Microsoft Entra ID is essential for ensuring secure, efficient, and scalable identity and access management across cloud and on-premises environments. By understanding the relationship between application objects and service principals, as well as leveraging tools like the Microsoft Entra admin center and Microsoft Graph PowerShell, administrators can effectively handle tasks such as application registration, deletion, restoration, and integration.
Whether working with preintegrated applications, custom-developed solutions, or on-premises apps, Microsoft Entra ID offers robust features to meet diverse organizational needs. By following best practices, you can streamline application management, maintain compliance, and enhance the overall security posture of your tenant.
This comprehensive approach empowers IT teams to maximize the benefits of Microsoft Entra ID, ensuring seamless application experiences for users while maintaining administrative control and security.









































0 Comments